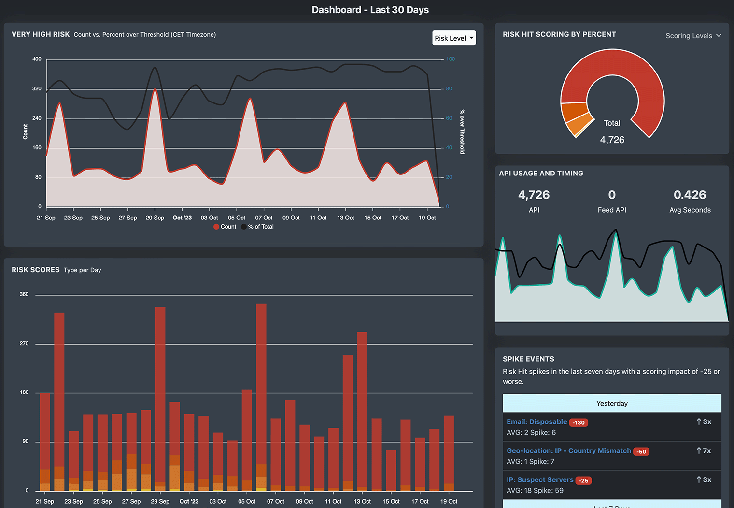
Block fake leads and fraud signups
Our cloud API identifies phishers, bots, spammers, fraudsters, high-risk users, and links lead quality to marketing performance.
Run hundreds of real-time risk assessments on every lead.
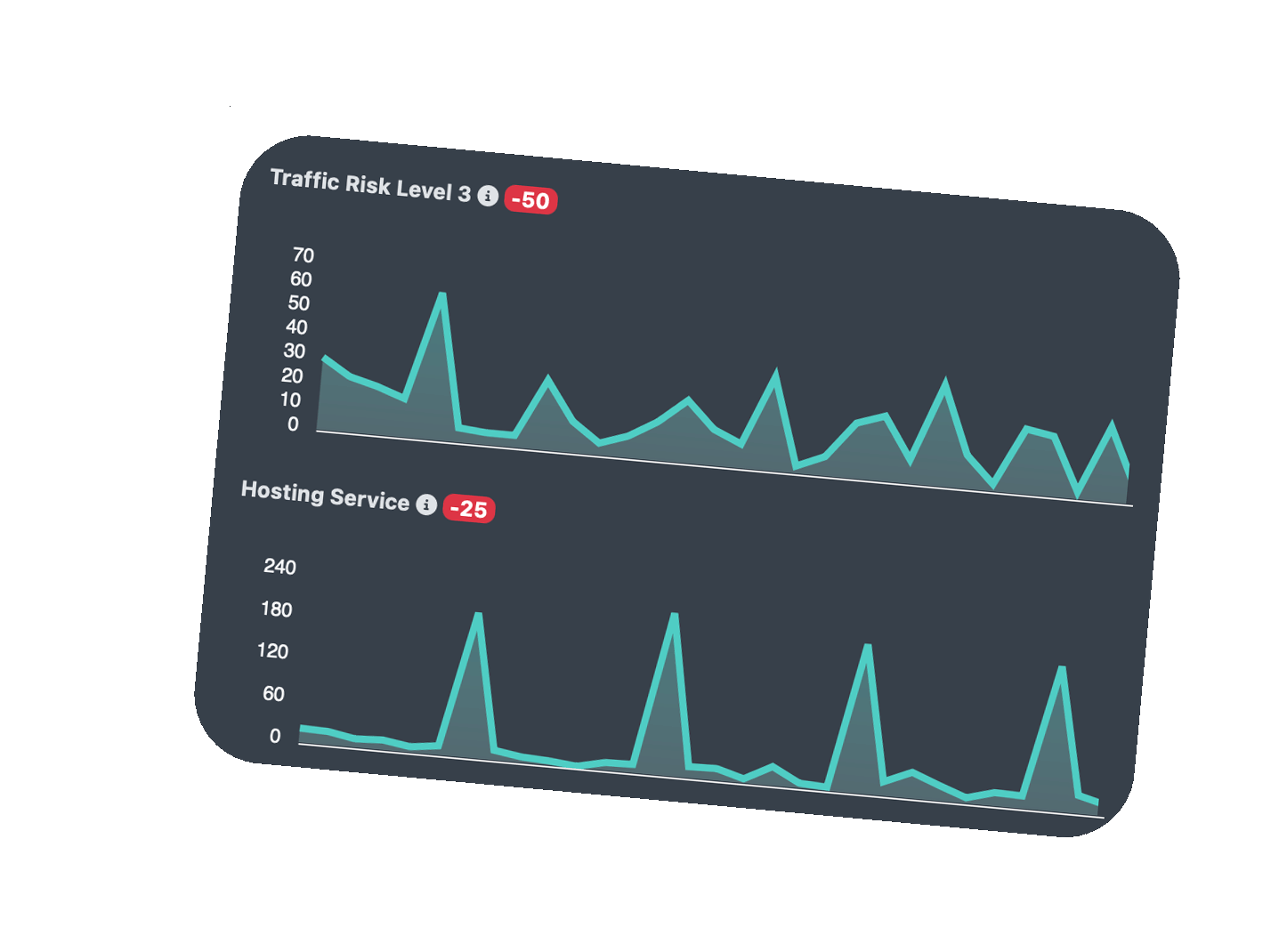
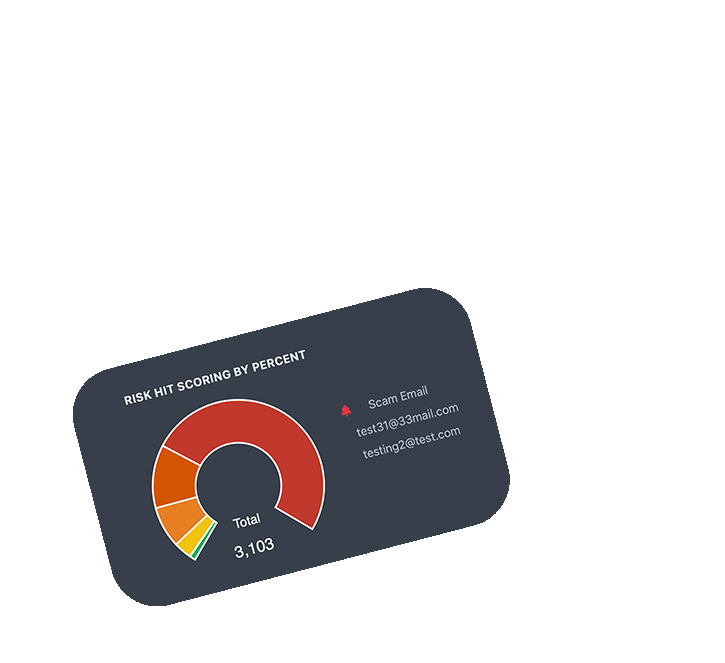
Make Onboarding Decisions Quickly
Vet every signup or lead for possible risks
- Stop Bogus Sign-ups
- Lead Scoring
- Tag High Risk Users
- Marketing Performance
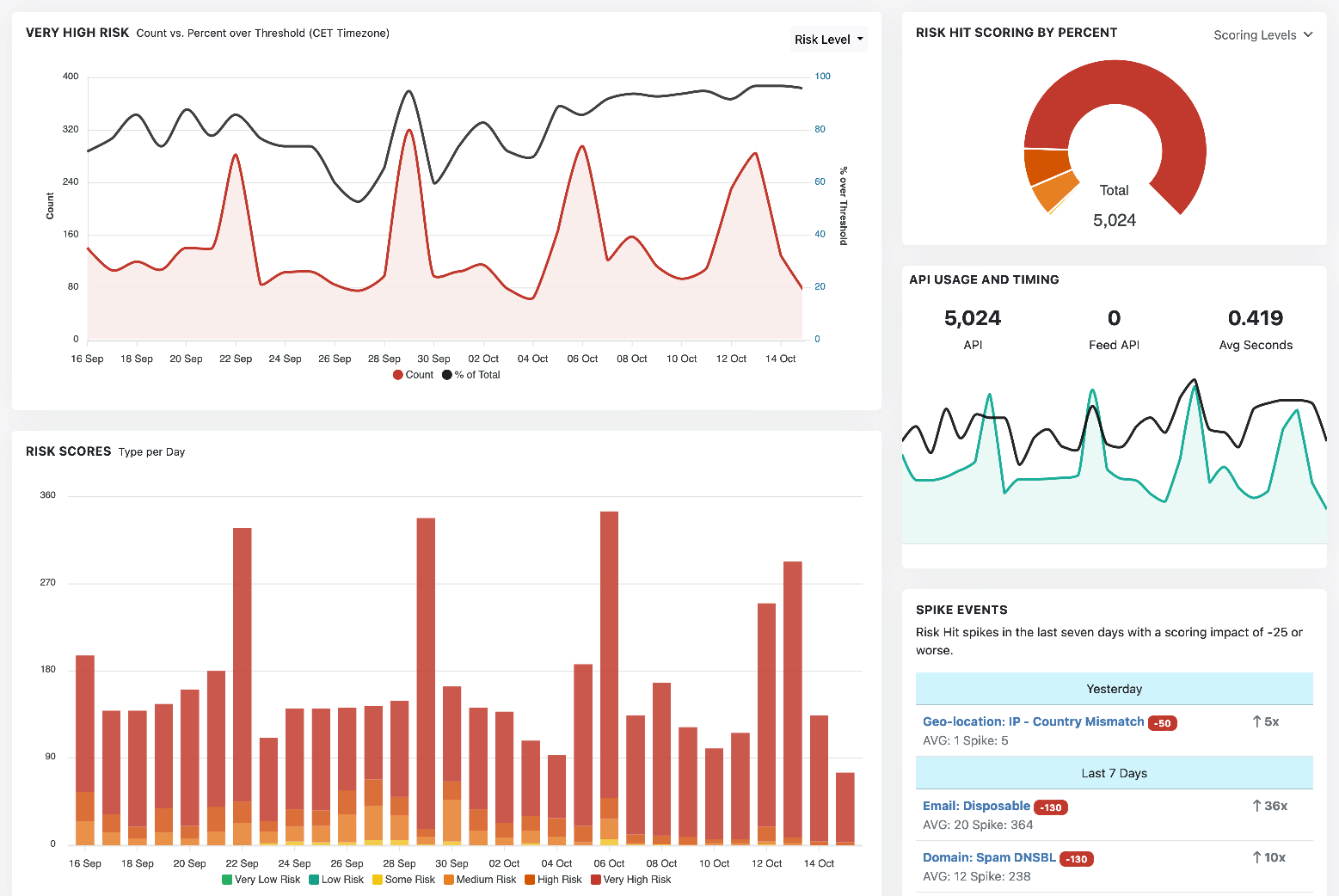
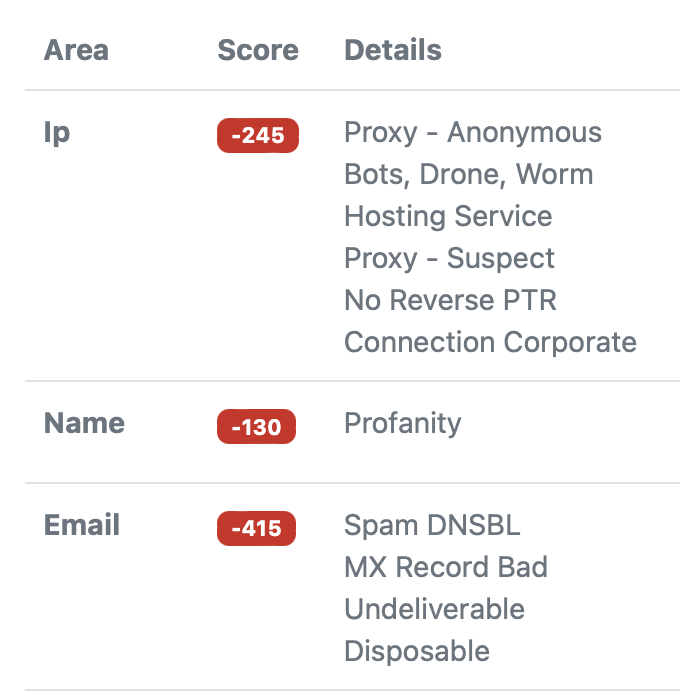
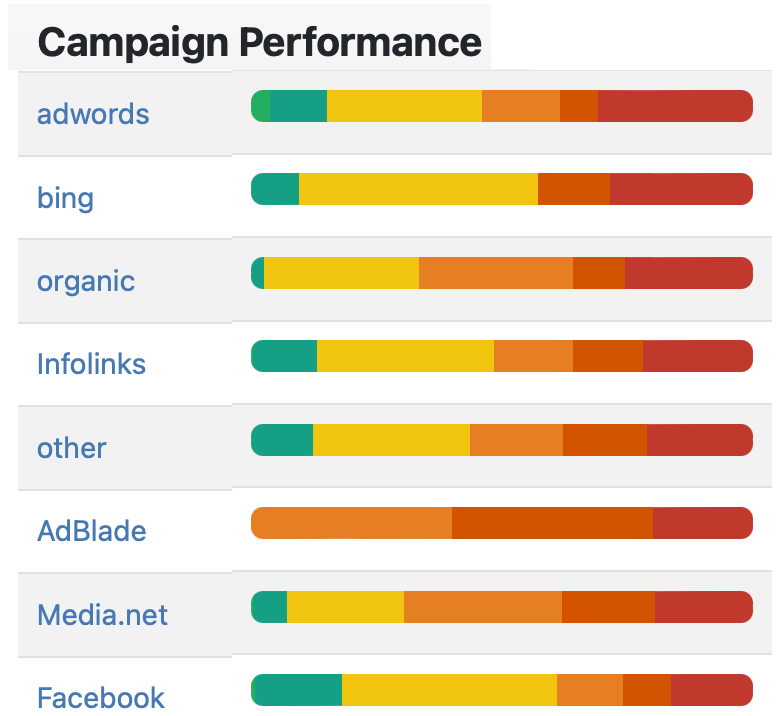
How Does It Work?
2
3